LinkDaddy Cloud Services: Secret Advancements and Most Recent Developments
LinkDaddy Cloud Services: Secret Advancements and Most Recent Developments
Blog Article
Achieve Business Connection With Secure Cloud Storage Solutions
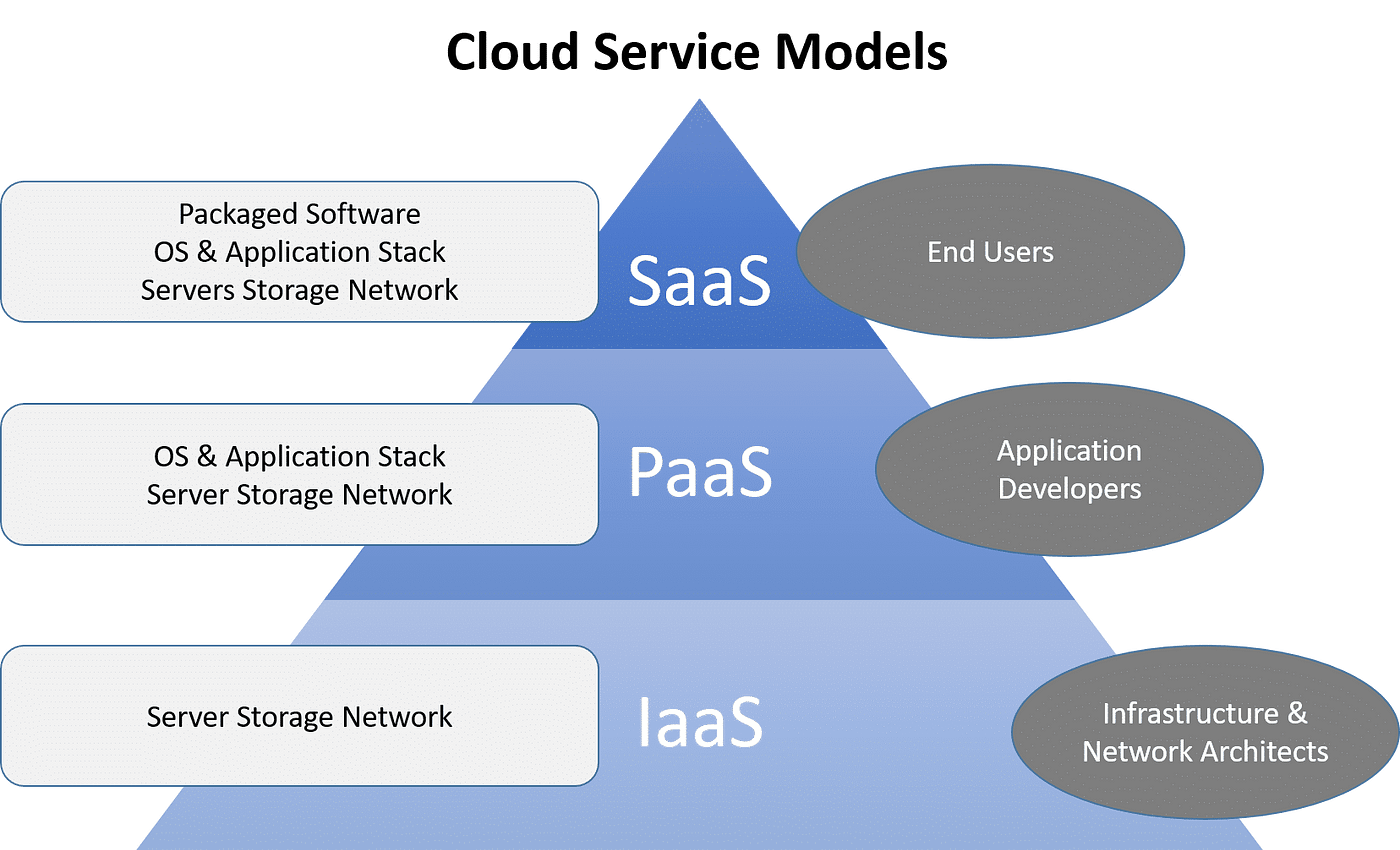
Advantages of Secure Cloud Storage
Undoubtedly, secure cloud storage uses services a wide variety of benefits in terms of data security and availability. By keeping information on reputable cloud platforms that utilize security and innovative safety procedures, companies can protect their information from unapproved gain access to or cyber dangers. In general, the advantages of safe cloud storage space translate into boosted data management, increased functional effectiveness, and enhanced safety for services of all sizes.
Trick Functions for Company Continuity
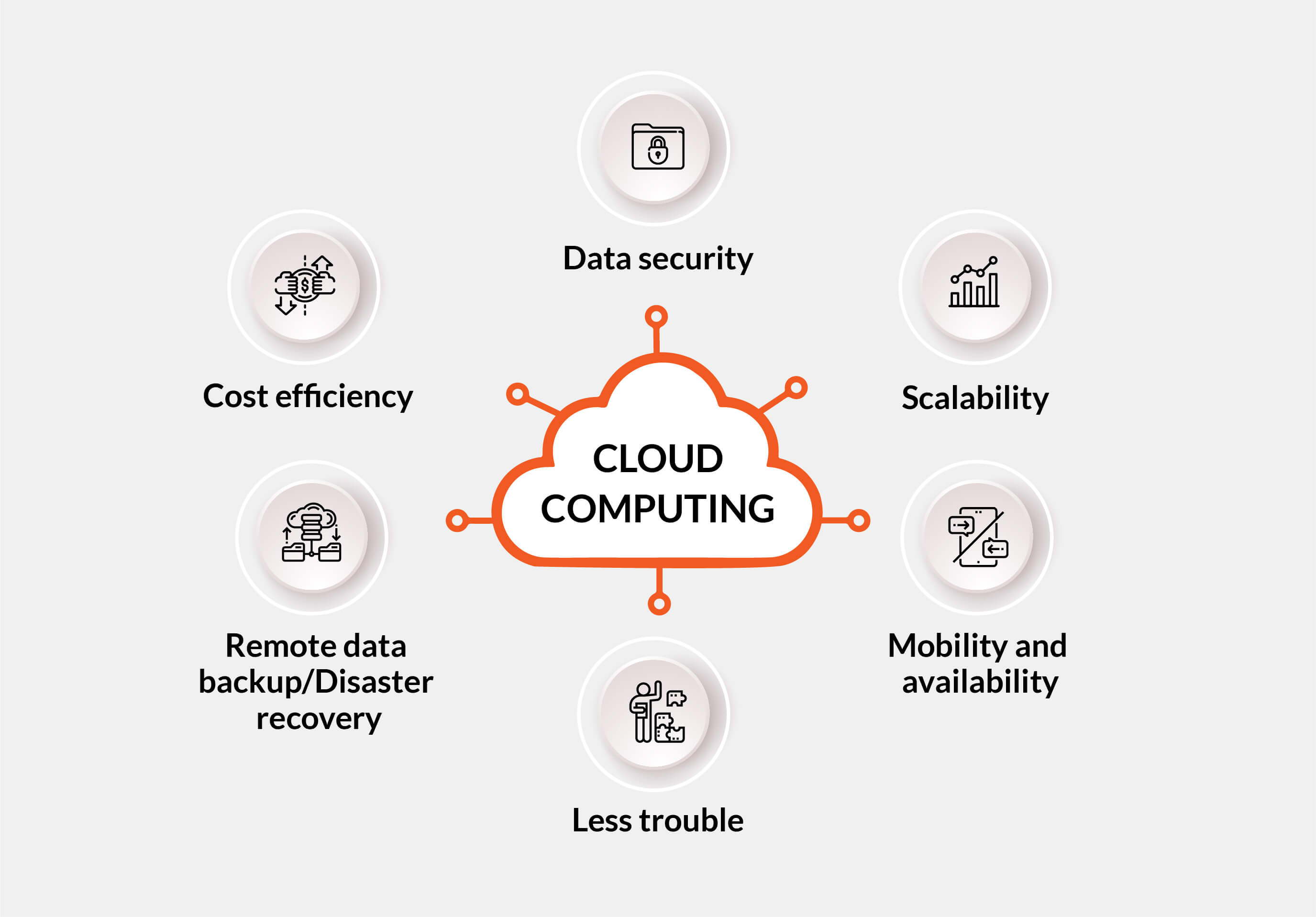
By distributing data across numerous web servers or data centers, businesses can minimize the threat of information loss and guarantee continuous accessibility to their info. In general, these essential features function with each other to develop an extensive company continuity approach that safeguards vital data and operations.
Relevance of Data File Encryption
In today's interconnected electronic landscape, protecting delicate information is extremely important, making the significance of data file encryption a fundamental element of maintaining data stability and safety. Information file encryption entails encoding info in such a way that just authorized events can access and understand it. By converting information into a secure style, file encryption serves as a shield versus unauthorized accessibility, decreasing the threat of data violations and cyber threats.

Disaster Healing Methods
A robust calamity healing strategy includes describing treatments to recover information, applications, and IT facilities in the event of a catastrophe. One vital element of an efficient strategy is normal information backups. By saving data in safe and secure cloud storage services, companies can ensure that essential details is shielded and conveniently obtainable in case of a catastrophe.
Choosing the Right Solution Supplier
To make certain seamless business continuity and efficient calamity recovery, choosing a ideal and dependable service provider for safe and secure cloud storage is critical. When choosing a cloud storage solution copyright, several vital variables need to be considered. Examine the service provider's security procedures. Ensure they utilize durable file encryption approaches, have rigorous gain access to controls, and abide with market laws to protect your information. Additionally, examine the company's information recovery abilities. A respectable provider should supply routine backups, redundancy actions, and effective recovery procedures to decrease downtime in case of a catastrophe.
Additionally, take into consideration the scalability and versatility of the cloud storage look at this now service. Your business requirements might evolve in time, so it's vital to pick a supplier that can suit your growing storage requirements and adapt to altering situations. Finally, analyze the service my response provider's performance history and reputation in the sector. Look for testimonials, reviews, and study to assess their dependability and efficiency. By very carefully examining these elements, you can choose a cloud storage space provider that aligns with your organization's requirements and guarantees continuous procedures when faced with potential disturbances.
Conclusion
Finally, safe cloud storage space solutions offer necessary benefits for accomplishing organization continuity, including improved security functions, smooth scalability, efficient partnership devices, durable data backup systems, and calamity recovery techniques. Information encryption plays a crucial role in securing delicate details, while choosing the right company is crucial to making certain compliance with policies and preserving operational efficiency. linkdaddy cloud services press release. Safe and secure cloud storage space is a valuable asset in today's digital landscape for guaranteeing nonstop company operations
Data backup mechanisms are essential for safeguarding against data loss due to system failures, cyber-attacks, or human mistakes. By distributing information throughout different web servers or information facilities, services can alleviate the danger of data loss and guarantee continual this hyperlink access to their information.In today's interconnected electronic landscape, guarding delicate info is vital, making the value of data file encryption an essential aspect of maintaining information stability and safety. By converting information right into a safe style, encryption acts as a guard versus unapproved accessibility, lowering the risk of information violations and cyber risks.
Conformity needs and information protection regulations usually mandate the usage of encryption to guard delicate info, highlighting its crucial duty in contemporary data safety methods.
Report this page